In this guide, we create an App Protection policy in order to demonstrate how to extend Data Protection and Data Loss Prevention (DLP) controls out to our managed and unmanaged devices.
App Protection for unmanaged devices is known as MAM without enrolment (MAM-WE). MAM-WE is commonly used for personal or bring your own devices (BYOD). Or, use on organisation-owned devices that need specific app configuration, or extra app security.
MAM-WE is also an option for users who don’t enroll their personal devices, but still need access to organisation email.
Create an App Protection Policy
From the home dashboard, navigate to Apps > App Protection Policies.
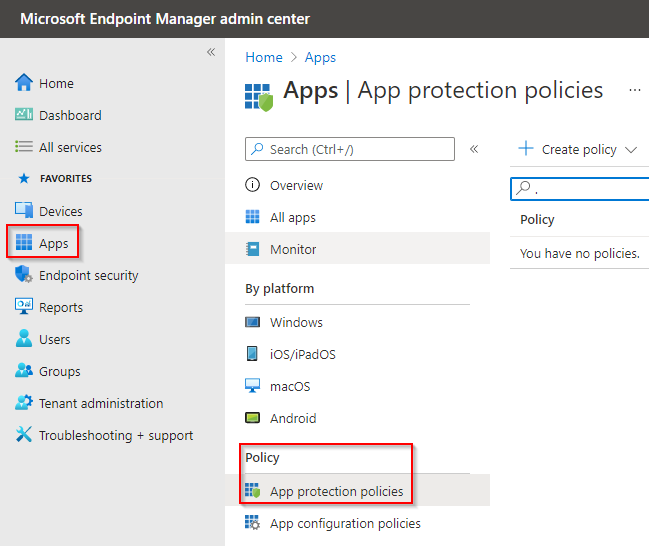
Select the ‘Add’ button and then select ‘iOS/iPadOS’.
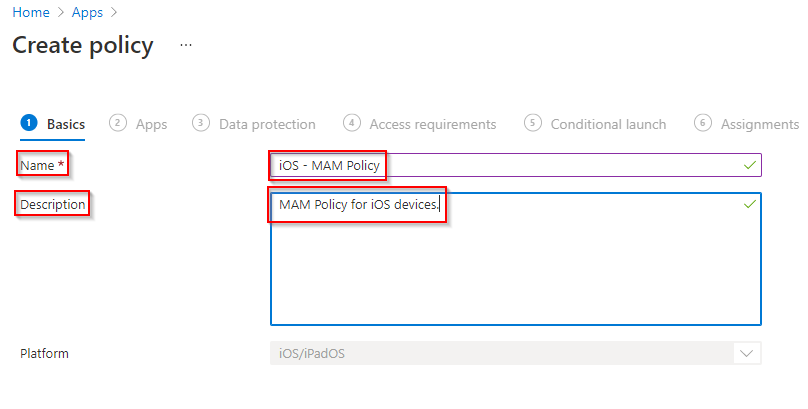
Set a Name and Description.
**Example**
Name: iOS – MAM Policy
Description: MAM Policy for iOS devices.
Select ‘Next’.
For the purposes of this training course, MAM will be targeted to both Managed and Unmanaged iOS devices.
The following App Protection settings will be set:
**Example**
Target to apps on all device types: Yes

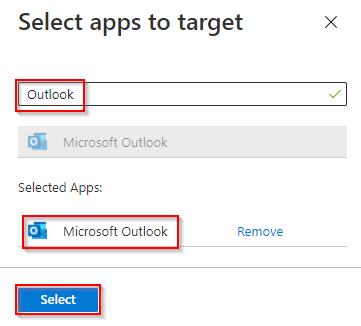
Press ‘Select Public Apps’ and then select Outlook from the list.

Select ‘Next’.
Data Transfer
- Backup org data to iTunes and iCloud backups: Block
- Send org data to other apps: Policy managed apps
- Select apps to exempt: Default
- Save copies of org data: Block
- Allow user to save copies to select services: OneDrive for Business & SharePoint
- Transfer telecommunication data to: Any dialer app
- Dialer App URL Scheme: None
- Receive data from other apps: Policy managed apps
- Open data into Org documents: Block
- Allow to user open data from select services: OneDrive for Business, SharePoint & Camera
- Restrict cut, copy, and paste between other apps: Policy managed apps
- Cut and copy character limit for any app: 0
- Third-party keyboards: Allow
Encryption
- Encrypt org data: Require
Functionality
- Sync policy managed app data with native apps: Allow
- Printing org data: Block
- Restrict web content transfer with other apps: Microsoft Edge
- Unmanaged browser protocol: None
- Org data notifications: Allow

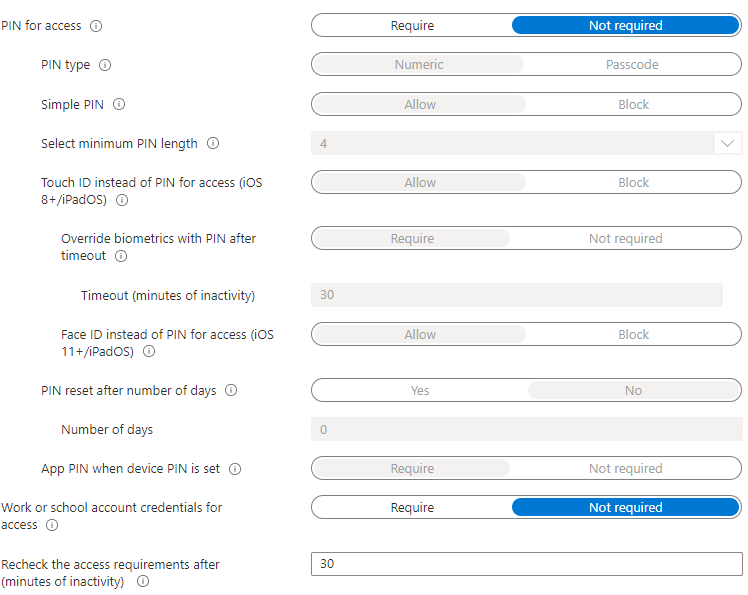
Access Requirements
- Pin for Acces: Not Required
- Work or school account credentials for access: Not Required
- Recheck the access requirements after (minutes of inactivity): 30
Conditional Launch
- Offline grace period: 720 – Block access (minutes)
- Offline grace period: 90 – Wipe data (days)
- Jailbroken/Rooted devices: Block access

Select ‘Next’.
Under Assignments, select ‘Add Groups’.
In this example, the ‘Corporate Devices’ group will be selected.
Select ‘Select’ to add your Azure AD Group.

Select ‘Next’ and then ‘Create’.
Once created, you will see the App Protection Policy appear in the list ready for use.

See in Action
App Protection can be validated on the device by the user. Observing our enroled device in Outlook, we can test cut, copy and paste restrictions that are being enforced by our App Protection policy.
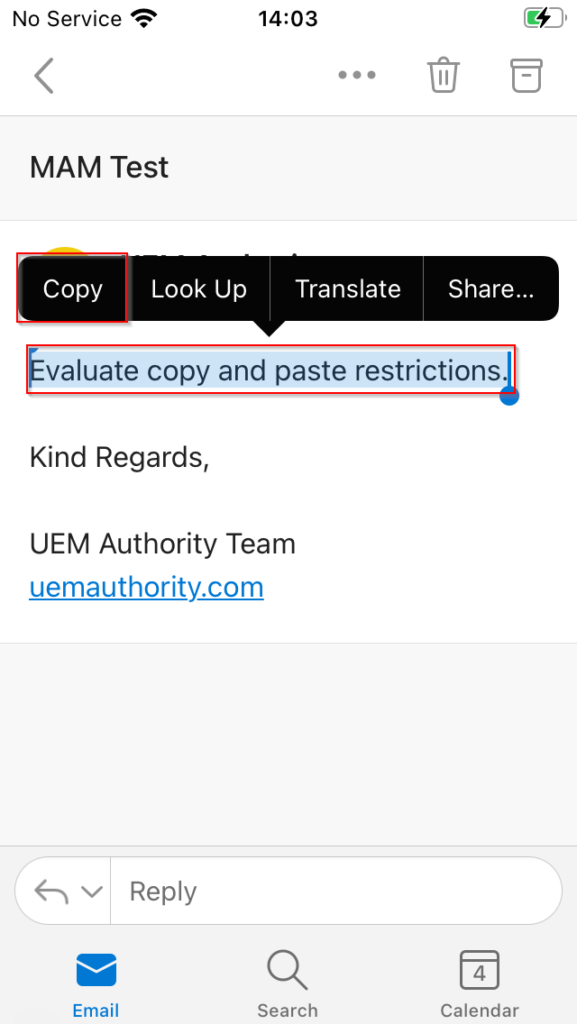
For the purposes of this demonstration, we have received an email from our fictional organisation that contains sensitive information. We will attempt to exfiltrate this information by means of Copy and Paste.
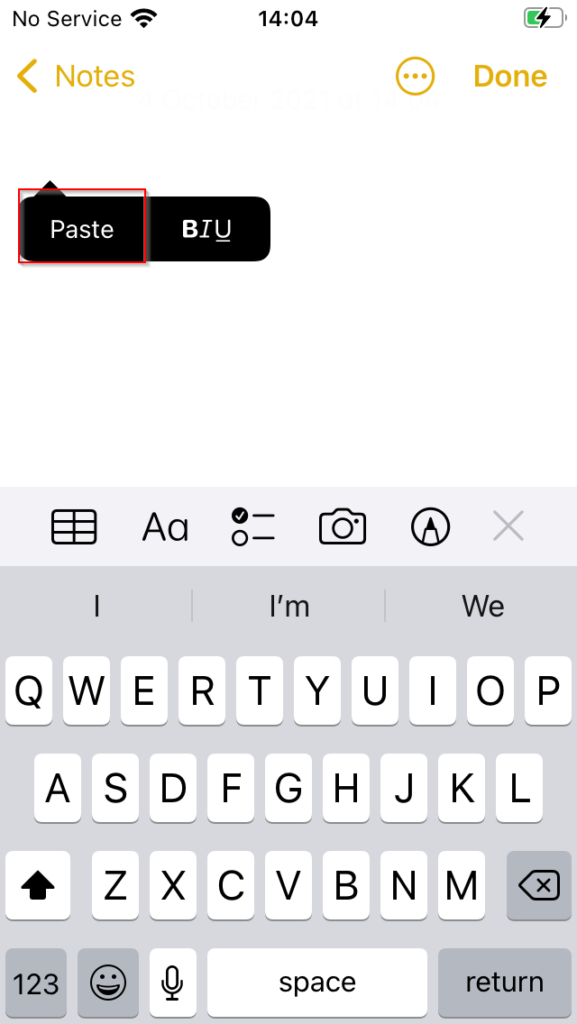
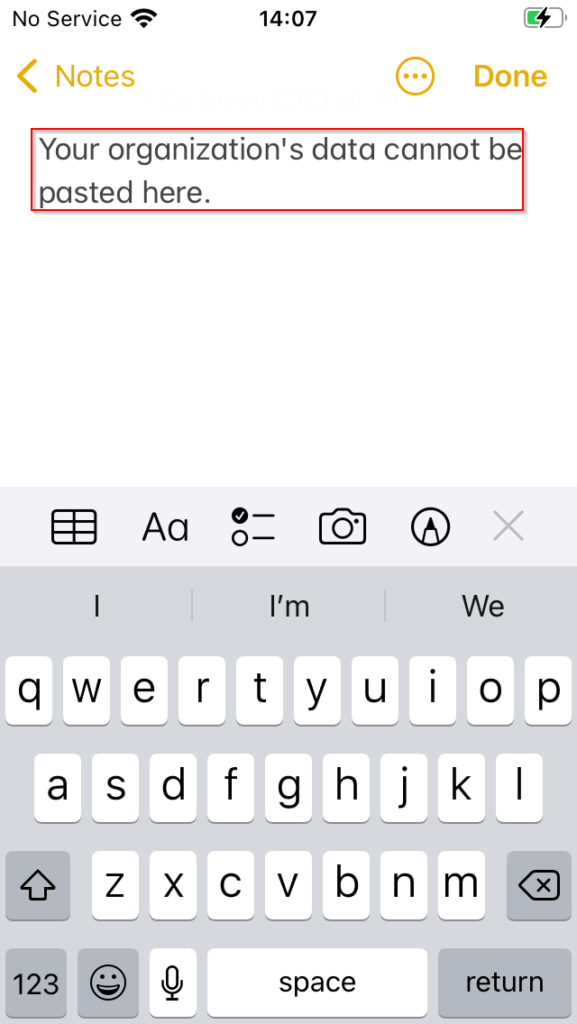
Copying text from the body of the email, we close Outlook and then open the native Notes app. Attempting to paste the copied information, App Protection replaces the original text in the clipboard cache with “Your orginastion’s data cannot be pasted here”.
Within the Endpoint Manager portal, we can validate which apps App Protection is applied to by app or user. Navigating to Apps > Monitor > App Protection Status > Reports.

Selecting the User Report, we choose the enroled user – johndoe@traininguemauthority.onmicrosoft.com.
The report shows iOS – MAM Policy is successfully applied against Microsoft Outlook.