Security incident and event management (SIEM) refer to the process of recording, monitoring, correlating, and analyzing the security events in an IT environment in real-time. No matter the size of a business, SIEM tools can have significant benefits for everything from compliance reporting to stopping attacks. Any managed services provider (MSP) can benefit from having SIEM software in its portfolio.
SIEM tools combine security information management (SIM) and security event management (SEM) functionalities. They use log data flows from different areas of an organization to create a real-time picture of potential threats to the IT environment, enabling your cybersecurity to be proactive rather than reactive. By relying on data from a variety of hosts in an IT environment, SIEM tools can provide you with a broad understanding of what is happening at every level of a business.
The SIEM process is one of the most critical branches of cybersecurity. By collecting, naturalizing, and correlating log data from an organization, SIEM tools help you reduce security breaches with proactive security.
Integration Advantages:
Data Aggregation and Visibility: Visibility into your entire IT environment is one of the biggest benefits of SIEM. This visibility goes hand in hand with the way that logs are normalized and correlated in a SIEM tool.
That’s why the SIEM capabilities that relate to data aggregation and normalization are so beneficial. Not only does a SIEM tool collect and store the data from the security tools in your IT environment in a centralized location, but it also normalizes them into a uniform format so you can easily compare the data. The tool also analyzes and correlates this data, finding connections that can help you detect security incidents quickly.
Incident Detection: Many of the hosts on your system that log security breaches don’t include built-in incident detection capabilities. That means they can observe events and produce log entries, but can’t analyze them for potentially suspicious activity. However, because SIEM tools correlate and analyze the log data that’s produced across hosts, they’re able to detect the incidents that might otherwise be missed—either because the relevant logs were not analyzed or because they were too widely separated between hosts to be detected.
There is a huge difference between detecting an attack as it’s occurring versus detecting it long after it has already succeeded. By detecting incidents that might otherwise go unnoticed until much later, the SIEM workflow can limit the scale of damage that might result from the threat.
Improved Efficiency: SIEM tools can significantly improve your efficiency when it comes to understanding and handling events in your IT environment. With SIEM tools, you can view the security log data from the many different hosts in your system from a single interface. This expedites the incident handling process in several ways. First, the ability to easily see log data from the hosts in your environment allows your IT team to quickly identify an attack’s route through your business. Second, the centralized data lets you easily identify the hosts that were affected by an attack.
Working more efficiently, especially when it comes to ongoing security incidents, is a huge asset for MSPs to be able to provide for their customers. By responding quickly to perceived events, SIEM tools can help you reduce the financial impact of a breach—as well as the amount of damage that occurs in the first place.
Simplified Compliance Reporting: Practically every business, no matter the size or the industry, has at least some regulations that it needs to comply with. Ensuring that you’re abiding by those regulations and that you can prove your compliance can be a difficult and time-consuming task. Luckily, thanks to the collection, normalization, and organization of log data, SIEM tools can help simplify the compliance reporting process. In fact, the benefits of SIEM tools as centralized logging solutions for compliance reporting are so significant that some businesses deploy SIEMs primarily to streamline their compliance reporting.
SIEM tools can save businesses both time and money by simplifying compliance reporting to make sure MSP customers are not in violation of any regulations. Without accurate reporting to prove compliance, businesses may face hefty fines and loss of accreditation. With SIEM tools, MSPs can easily generate reports that provide details on their customers’ compliance with the relevant regulatory protocols.
Policy Violation Notifications: A SIEM system in place will assure that any policy violation activity is reported quickly so that immediate countermeasures can be deployed. SIEM systems come with an automated alerting mechanism that makes this process easy. You can use the SIEM altering tool to get emails and dashboard notifications. This helps in preventing chronic violations and taking strict action against users for regular violations as we already integrated Workspace ONE UEM and Workspace ONE Access with the Directory Service, please review it from the basic guide: Deploy Workspace One 101 – For Beginners.
Forensic Analysis of Major Security Breaches: SIEM systems are designed for identifying patterns in cyber-attacks to prevent the IT assets of an organization. From compliance management to real-time monitoring, its ultimate goal is to enhance the security practices of your organization. With advanced tools and a rich set of features, you need expertise for integrating SIEM into your existing infrastructure. Vendors offering SIEM as a service can analyze your business activities and integrate cost-efficient SIEM solutions for your corporate security.
Configure Syslog:
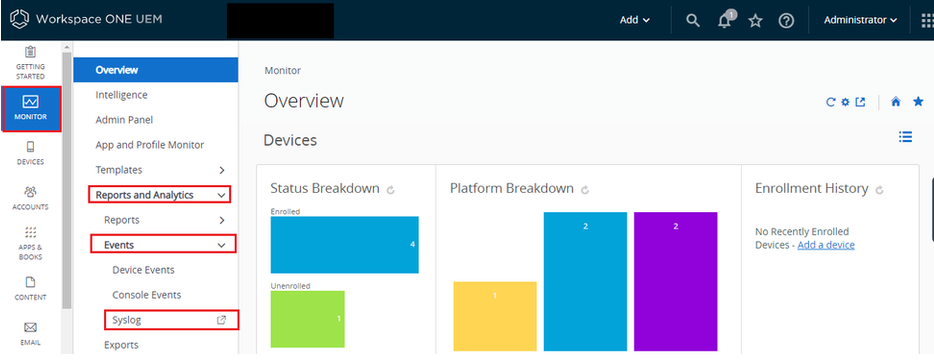
· Click Monitor.
· Click Reports & Analytics.
· Click Events.
· Click Syslog.
· Set the Syslog Integration to Enabled.
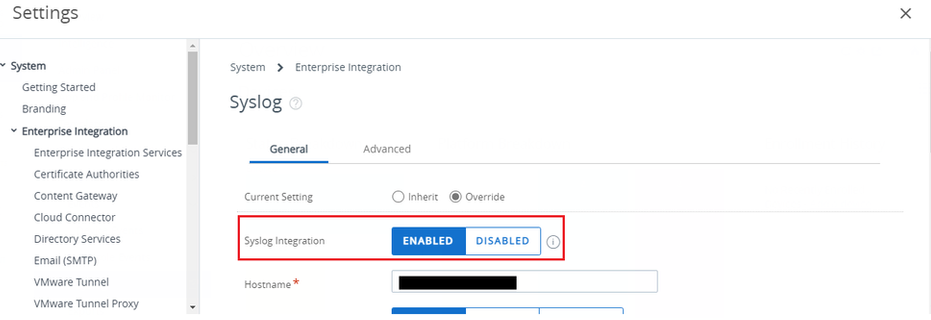
· In General Tab, enter the following data:
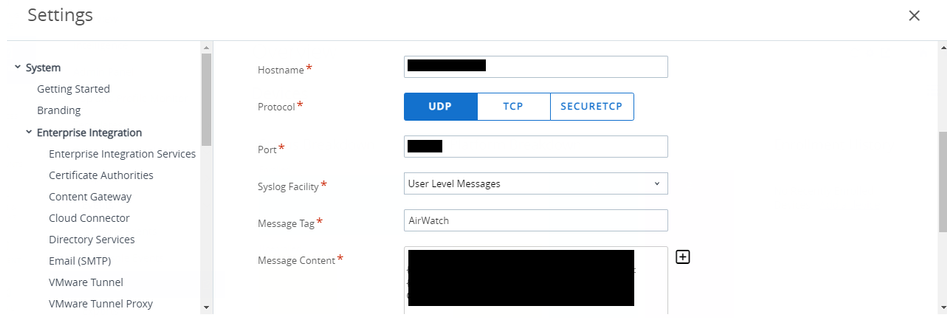
o Hostname which is your SIEM URL.
o Protocol: Select the required protocol from available options (UDP, TCP, or Secure TCP) to send the data. We support TLS v1.0, TLS v 1.1, and TLS v1.3.
o Port: Enter the port number to communicate with the SIEM tool in the Port text box.
o Syslog Facility: select the facility level for the feature from the Syslog Facility menu. The Syslog protocol defines the Syslog facility.
o Message Tag: Enter a descriptive tag to identify events from the Workspace ONE UEM console in the Message Tag text box. For example, “AirWatch”.
o Message Content: Enter the data to include in the transmission in the Message Content text box. This is how the message data gets formatted when sent using Syslog to your SIEM tool. Use lookup values to set the content. For secure TCP, Newline (CRLF) formatting using Enter, \n, \r does not work and gets automatically converted to tab, \t for secure TCP.
· Click Save and use the Test Connection button to ensure successful communication between the Workspace ONE UEM console and the SIEM tool.
Configure the Scheduler Syslog Task:
You can configure the Scheduler Syslog Task for on-premises deployments. This task sets the intervals at which the AirWatch Console sends requests to the SIEM tool for data.
· From Workspace ONE UEM console, go to GROUPS & SETTINGS.
· Click All settings.
· Click Admin.
· Click Schedule.
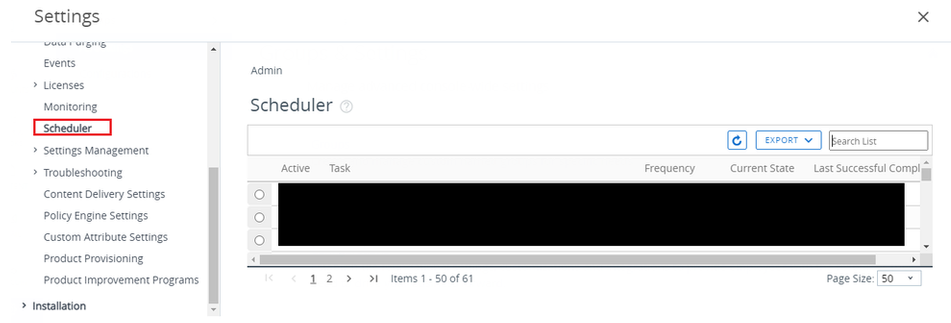
· Click Edit for Syslog task.
· Define the interval at which the Console sends data to the options configured in the Syslog feature in the Recurrence Type setting.
· Define Range setting.
· Click Save.
You have successfully configured the Scheduler Syslog Task.
